Implementing, Monitoring, and Troubleshooting
Security:
Active Directory Overview:
Active Directory (AD) srevices provide a single point
of network management, allowing you to add, remove, and
relocate resources easily. It offers significant
enhancements over the limitations of the older Windows
NT domain based security model. It's features are:
- Simplified Administration - AD provides a
single point of logon for *all* network resources -
an administrator can logon to one computer and
administer objects on any computer in the network.
- Scalability - NT 4 domains had a
practical limitation of about 40,000 objects. AD
scales to millions of objects, if needed.
- Open standards support - uses DNS as it's
domain naming and location service so Windows 2000
domain names are also DNS domain names. Support for
LDAP v2 and v3 makes AD interoperable with other
directory services that support the same, such as
Novell's NDS. HTTP support means that AD can be
searched using a Web browser. Kerberos 5 support
provides interoperability with other products that
use the same authentication mechanism.
Active Directory Structure:
- Object - distinct named set of attributes
that represents a network resource such as a
computer or a user account.
- Classes - logical groupings of objects
such as user accounts, computers, domains or
organizational units.
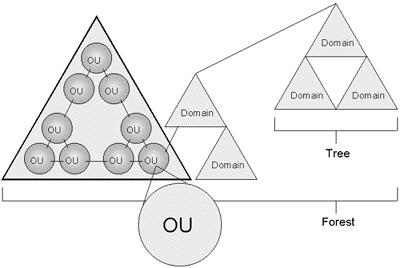
- Organizational Unit (OU) - container used
to organize objects inside a domain into logical
administrative groups such as computers, printers,
user accounts, file shares, applications and even
other OUs.
- Domain - all network objects exist within
a domain with each domain storing information only
about the objects it contains. A domain is a
security boundry - access to objects is controlled
by Access Control Lists (ACLs). ACLs contain the
permissions associated with objects that control
which users or types of users can access them. In
Windows 2000, all security policies and settings
(like Administrative rights) do not cross from one
domain to another. The domain admin only has right
to set policies within his/her domain.
- Tree - a grouping or hierarchical
arrangement of one or more Windows 2000 domains that
share a contiguous names space (e.g.
cramsession.brainbuzz.com, sales.brainbuzz.com, and
jobs.brainbuzz.com). All domains inside a single
tree share a common schema (formal definition of all
object types that can be stored in an AD deployment)
and share a common Global Catalog.
- Forest - a grouping or hierarchical
arrangement of one or more domain trees that form a
disjointed namespace (e.g. cramsession.com and
brainbuzz.com). All trees in the forest share a
common schema and Global Catalog, but have different
naming structures. Domains in a forest operate
independently of each other, but the forest enables
communication across the domains.
- Sites - combination of one or more IP
subnets connected by high-speed links. Not part of
the AD namespace, and contains only computer objects
and connection objects used to configure replication
between sites.
Site Replication:
- Active Directory information is replicated between
Domain Controllers (DCs) and ensures that changes to
a domain controller are reflected in all DCs within
a domain. A DC is a computer running Windows 2000
server which contains a replica of the domain
directory (member servers do not).
- DCs store a copy of all AD information for their
domain, manage changes to it and copy those changes
to other DCs in the same domain. DCs in a domain
automatically copy all objects in the domain to each
other. When you change information in AD, you are
making the change on one of the DCs.
- Administrators can specify how often replication
occurs, at what times, and how much data can be
sent.
- DCs immediately replicate important changes to AD
like a user account being disabled.
- AD uses multimaster replication meaning
that no one DC is the master domain controller - all
DCs within a domain are peers (however there are
still some roles called Operations Master roles that
can only be held by one DC at a time).
- Having more than one DC in a domain provides
fault-tolerance. If a DC goes down, another is able
to continue authenticating logins and providing
required services using it's copy of AD.
- Replication is automatically generates a ring
topology for replication in the same domain and
site. The ring ensures that if one DC goes down, it
still has an available path to replicate it's
information to other DCs.
Active Directory Concepts:
Schema - contains a formal
definition of contents and structure of AD such as
attributes, classes and class properties. For an object
class, the schema defines what attributes an instance of
a class must have, additional attributes that are
allowed and which object class can be it's parent.
Installing AD on the first computer in a network creates
the domain and default schema which contains commonly
used objects. Extensions can be made to the schema
whenever needed. By default, write access to the schema
is limited to members of the Administrators group. (KB# Q229691)
Global Catalog - central
repository of info about object in a tree or forest. AD
automatically creates a global catalog from the domains
that make up AD through the replication process.
Attributes stored in the global catalog are usually
those most often used in Search operations (like user
names, logon names, etc.) and are used to locate a full
replica of the object. Because of this, the global
catalog can be used to find objects anywhere in the
network without replication of all information between
DCs.
Active Directory Naming Conventions:
- Distinguished Name (DN)
- every object in AD has one. Uniquely identifies
object and contains sufficient info for an AD client
to retrieve it from the Directory. Includes the name
of the domain that holds the object and also the
complete path through the container hierarchy to it.
DNs must be unique - AD will not allow duplicates.
- Relative Distingushed Name (RDN)
- if the DN is unknown, you can still query an
object by it's attributes. The RDN is a part of the
name that is an attribute of the object itself (e.g.
a user's first name and location).
- Globally Unique Identifier (GUID)
- unique 128-bit number assigned to objects when
they are created. The GUID never changes so even if
the object is renamed or moved, the GUID can be used
to locate it.
- User Principal Name (UPN)
- "friendly name" given to a user account
(e.g. johndoe@brainbuzz.com).
Local user accounts: (KB# Q217050)
- Resides only on the computer where the account was
created in it's local security database. If computer
is part of a peer-to-peer workgroup, accounts for
that user will have to be created on each additional
machine that they wish to log onto locally. Local
accounts cannot access Windows 2000 domain resources
and should not be created on computers that are part
of a domain.
- Domain user accounts reside in AD on domain
controllers and can access all resources on a
network that they have been accorded priveleges for.
- Built in user accounts are Administrator (used for
managing the local system) and Guest (for occasional
users - disabled by default)
- Usernames cannot be longer than 20 characters and
cannot contain the following illegal characters:
" / \ [ ] : ; | = , + * ? < >
- User logon names are not case sensitive. You can
use alphanumeric combinations to increase security,
if desired.
- Passwords can be up to 128 characters (we're not
kidding!!) but Microsoft recommends limiting them to
about eight characters.
- The same characters that are considered illegal in
usernames are also verbotten for use in passwords
- User accounts are added and configured through the
Computer Management snap-in.
- MS recommends that users be encouraged to store
their data in their My Documents folder which is
automatically created within their profile folder
and is the default location that Microsoft
applications use for storing data. This folder
should not be used with roaming profiles unless it
has been redirected to a network file share.
- Creating and duplicating accounts requires only
two pieces of information: username and password.
Disabling an account is typically used when someone
else will take the user's place or when the user
might return.
- Delete an account only when absolutely necessary
for space or organization purposes.
- When copying a user account, the new user will
stay in the same groups that the old user was a
member of. The user will keep all group rights that
were granted through groups, but lose all individual
rights that were granted specifically for that user.
Local user authentication:
Built-in local groups:
| Local
Group |
Description |
| Administrators |
Can
perform all administrative tasks on the local
system. The built-in Administrator account is
made a member of this group by default. |
| Backup
Operators |
Can use
Windows Backup to back up and restore data on
the computer |
| Guests |
Used
for gaining temporary access to resources for
which the Administrator has assigned
permissions. Members can't make permanent
changes to their desktop environment. When a
computer or member server running Client for
MS Networks joins a domain, Windows 2000 adds
Domain Guests to the local Guests group. |
| Power
Users |
Can
create and modify local user accounts on the
computer, share resources and can install
drivers for legacy software. |
| Replicator |
Supports
file replication in a domain |
| Users |
Can
perform tasks for which they have been
assigned permissions. All new accounts created
on a Windows 2000 machine are added to this
group. When a computer or member server
running Client for MS Networks joins a domian,
Windows 2000 adds Domain users to the local
Users group. |
Built-in system groups:
| Local
Group |
Description |
| Everyone |
Includes
all users who access the computer. |
| Authenticated
Users |
Includes
all users with a valid user account on the
computer or domain - used to prevent anonymous
access to a resource |
| Creator
Owner |
Includes
user account for the user who created or took
ownership of a resource. |
| Network |
Includes
any user with a current connection from
another computer on the network to a shared
resource on the computer |
| Interactive |
Includes
the user account for the user who is logged on
at the computer. Members of this group gain
access to the resources on the computer they
are physically located at. |
| Anonymous
Logon |
Any
user that Windows 2000 didn't authenticate. |
| Dialup |
Any
user who currently has a dial-up connection. |
Group Policy:
Group Policies are a collection of user environment
settings that are enforced by the operating system and
cannot be modified by the user. User profiles refer to
the environment settings that users can change.
System Policy Editor (poledit.exe)
- Windows NT 4, Windows 95 and Windows 98 all use
the System Policy Editor (poledit.exe) to specify user
and computer configuration that is stored in the
registry.
- Not secure because settings can be changed by a
user with the Registry Editor (regedit.exe).
Settings are imported/exported using .ADM templates.
- Are considered "undesirabley persistant"
as they are not removed when the policy ends.
- Windows 2000 comes with system.adm (system
settings), inetres.adm (Internet Explorer settins)
and conf.adm (NetMeeting settings) although the
latter is not loaded by default.
Group Policy snap-in (gpedit.msc) -
Exclusive to Windows 2000 and supercedes the System
Policy Editor. Uses Incremental Security Templates.
- Should only be applied to Windows 2000 systems
that have been clean installed onto an NTFS
partition. NTFS computers that have been upgraded
from NT4 or earlier, only the Basic security
templates can be applied.
- Settings can be stored locally or in AD. Are
secure and cannot be changed by users - only
Administrators.
- More flexible than System Policies as they can be
filtered using Active Directory.
- Settings are imported/exported using .INF files.
The Group Policy snap-in can be focused on a local
or remote system.
Incremental Security Templates for Windows 2000:
| Template: |
Filename: |
Description: |
| Compatibility |
compatws.inf |
Compatibility
template, but also referred to in MS
documentation as Basic template. Sets up
permissions for local users group so that
legacy programs are more likely to run. Not
considered a secure environment. |
| Secure |
securews.inf |
Increases
security settings for Account Policy and
Auditing. Removes all members from Power Users
group. ACLs are not modified. |
| High
Secure |
hisecws.inf |
Secure
template provided for Workstations running in
W2K native mode only. Requires all network
communications to be digitally signed and
encrypted. Cannot communicate with downlevel
Windows clients. Changes ACLs to give Power
Users ability to create shares and change
system time. |
Local Group Policy:
- There are two types of Group Policy objects: local
Group Policy objects and non-local Group Policy
Objects. Each Windows 2000 system can have only one
local Group Policy object.
- Order of application is Local, Site, Domain and
Organizational Unit. Local Policies have the least
precedence whereas OU Policies have the highest.
Non-local Group Policy (stored in Active Directory):
- Can be linked to a site with AD Sites and Services
and applies to all domains at the site
- When applied to a domain it affects all users and
computers in the domain and (by inheritance) all
users and computers in Organizational Units.
Config.pol, NTConfig.pol and Registry.pol:
- Windows 2000 uses the registry.pol
format. Two files are created, one for Computer
Configuration (stored in the \Machine subdirectory)
and one for User Configuration (stored in the \User
subdirectory).
- Registry.pol files can be used with Windows 95/98,
Windows NT 4.0 and Windows 2000 as it is a text file
embedded with binary strings. NTConfig.pol is a
binary file whereas Config.pol is a text file.
- .POL files can be viewed using the regview.exe
tool from the W2K Resource Kit. Viewing
them does not apply them to the registry.
Security configuration:
Security Configuration and Analysis snap-in - Stand
alone MMC snap-in that can configure or analyze W2K
security. Based on contents of a security template
created using Security Templates snap-in. There is a
text based version of this tool that can be run from the
command line - secedit.exe.
By default, Windows 2000 Professional doesn't require
users to press CTRL-ALT-DEL to logon. Increase security
by disabling this feature and forcing users to press
CTRL-ALT-DEL, which is a key combination recognized only
by Windows (set using the Group Policy snap-in).
To disable access to the workstation, but allow
programs to continue running, use the Lock Workstation
option (from the CTRL-ALT-DEL dialog box).
To disable access to the workstation, and not allow
programs to continue running, use the Logoff option
(from the CTRL-ALT-DEL dialog box).
To lock the workstation after a period of idle time,
use a screensaver password.
Auditing can be enabled by clicking Start >
Programs > Administrative Tools > Local Security
Policy. In the Local Security Settings window
double-click Local Policies and then click Audit Policy.
Highlight the event you want to audit and on the Action
menu, click Security. Set the properties for each object
as desired then restart computer for new policies to
take effect.
Clear the Virtual Memory Pagefile when the system
shuts down. By default it is not cleared, but this can
be changed under Local Security Policy Settings and will
prevent unauthorized person from extracting information
from your system's pagefile. (KB# Q182086)
Prevent the last user name from being displayed at
logon (W2K Pro does this by default). Use the Group
Policy snap-in, Local Computer Policy, to change this.
When using Event Viewer, only local administrators
can see the security log, but anyone (by default) can
view other logs.
Encrypting File System (EFS): (KB# Q223316
& Q230520)
About EFS:
- Only works on Windows 2000 NTFS partions (NTFS
v5).
- Encryption is transparent to the user.
- Uses public-key encryption. Keys that are used to
encrypt the file are encrypted by using a public key
from the user's certificate.The list of encrypted
file-encryption keys is kept with the encrypted file
and is unique to it. When decrypting the file
encryption keys, the file owner provides a private
key which only he has. (KB# Q241201
& Q230490)
- If the owner has lost his private key, an
appointed recovery system agent can open the file
using his/her key instead. (KB# Q242296)
- There can be more than one recovery agent, but at
least one public recovery key must be present on the
system when the file is encrypted.
- EFS resides in the Windows OS kernel and uses the
non-paged memory pool to store file encryption keys
- this means no one will be able to extract them
from your paging file.
- Encrypted files can be backed up using the Backup
Utility, but will retain their encrypted state as
access permissions are preserved. (KB# Q227825
& Q223178)
- Microsoft recommends creating an NTFS folder and
encrypting it. In the Properties dialog box for the
folder click the General tab then the Advanced
button and select the "Encrypt Contents To
Secure Data" check box. The folder isn't
encrypted, but files placed in it will be
automatically encrypted. Uncheck the box if you want
to decrypt the file.
- Default encryption is 56-bit. North Americans can
upgrade to 128-bit encryption.
- Compressed files can't be encrypted and vice
versa. (KB# Q223093)
- You can't share encrypted files
- Use the Cipher command to work with encrypted
files from the command line. (KB# Q229530)
& Q229546)
- Encrypted files are decrypted if you copy or move
them to a FAT volume (remember that floppies are
always formatted as FAT).
- Cut and paste to move files into an encrypted
folder - if you drag and drop files, the files are
not automatically encrypted in the new folder.
- The efsinfo.exe utility in the
W2K Resource Kit allows an administrator to
determine information about encrypted files (KB# Q243026)
Using the CIPHER command:
| Switch |
Function |
| /a |
performs
the specified operation on files as well as
folders |
| /d |
decrypts
specified folders and they are marked so files
added to them will not be encrypted |
| /e |
encrypts
specified folders and they are marked so any
files added later on are encrypted as well |
| /f |
forces
encryption operation on all specified files,
even those already encrypted |
| /h |
shows
files with hidden/system attributes (not shown
by default) |
| /i |
specified
operation continues even after errors have
been reported |
| /k |
creates
a new file encryption key for user running
Cipher command - cannot be used in conjunction
with other options |
| /q |
reports
only essential information |
| /s |
applies
the specified operation to sub-folders as well |
| file_name |
specifies
a pattern, file, or folder |
IPSec: (KB# Q231585)
IPSec can be implemented in a Windows 2000 domain
using Active Directory or on a Windows 2000 machine
through it's Local Security settings. It is not
available for Windows 95/98 or Windows NT.
IPSec itself is a protocol, not a service. It
consists of two separate protocols, Authentication
Headers (AH) and Encapsulated Security Payload (ESP). AH
provides authentication, integrity and
anti-replay but does not encrypt data and is used
when a secure connection is needed but the data itself
is not sensitive. ESP provides the aforementioned plus confidentiality
(data encryption) and is used to protect sensitive or
proprietary information but is associated with greater
system overhead for encrypting and decrypting data.
Supported IPSec authentication methods are Kerberos
v5 Public Key Certificate Authorities, Microsoft
Certificate Server, and Pre-shared Key. (KB# Q240262)
The IPSec Policy Agent is a Windows 2000 service that
runs within the LSASS.EXE process and shows up in the
Services snap-in in MMC. It is loaded and started at
system startup and retrieves an IPSec policy from either
Active Directory or the local registry. After the IPSec
Policy has been obtained, it will be applied to *all* IP
traffic sent or received by that system (default
behavior - IPSec policy can be modified to allow
"soft associations" KB# Q234580).
Before two computers can communicate they must
negotiate a Security Association (SA). The SA defines
the details of how the computers will use IPSec, with
which keys, key lifetimes, and which encryption and
authentication protocols will be used.
When participating in a Windows 2000 domain, IPSec
policies are stored in Active Directory. Without AD,
they are stored in these registry keys... (KB# Q231588)
Group Policy:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent\Policy\Cache
Local Policy:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent\Policy\Local
Use IPSec Monitor (ipsecmon.exe) to view
status of IPSec on a Windows 2000 system.Windows 2000
Server Network Monitor can be used to view AH and ESP
packets (but not ESP packet data). IPSec Policy Agent
logs to the IPSECPA.LOG file. (KB# Q231587
& Q234581)